SHI and CrowdStrike: A powerful partnership in cybersecurity
SHI and CrowdStrike join forces to deliver next-generation cybersecurity, protecting your organization’s most vital assets from sophisticated and ever-evolving threats. By combining SHI’s technology expertise with CrowdStrike’s world-class endpoint protection, actionable threat intelligence, and real-time rapid response, we empower your business to operate securely, adapt quickly, and stay resilient in today’s dynamic digital landscape.
Benefits of CrowdStrike solutions through SHI
Identity protection
Provides deep visibility into identity based incidents and anomalies across a complex hybrid identity landscape, comparing live traffic against behavior baselines and policies to detect attacks and lateral movement in real time.
Next-gen SIEM
Stop the breach and respond in seconds with the world’s most complete AI-native SOC platform. CrowdStrike replaces legacy SIEMs with a modern security analyst experience delivered through a single console, with all critical data and threat intelligence already integrated into the CrowdStrike Falcon® platform.
Cloud security
Unprotected cloud workloads are a massive risk. See how Falcon Cloud Security's 1-click capability delivers end-to-end agentless visibility to automated agent deployment to secure your runtime environment.
Discover what's next with SHI and Crowdstrike
Cross domain attacks
CrowdStrike Falcon Endpoint Security
See CrowdStrike Falcon Endpoint Security in action as it detects and stops sophisticated adversaries like Scattered Spider in real time. This video demonstrates how Falcon’s unified platform leverages advanced AI, elite threat intelligence, and intuitive dashboards to visualize attack chains, accelerate investigations, and automate effective responses. Learn how CrowdStrike’s Charlotte AI deciphers complex threats and how seamless integration streamlines threat detection, response, and remediation across your environment.
Advanced endpoint protection
Securing AI
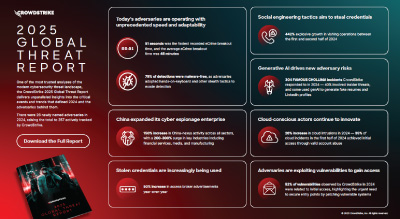
CrowdStrike 2025 Global Threat Report
The CrowdStrike 2025 Global Threat Report analyzes key cyber threats and adversary trends from 2024, highlighting the rise of enterprising adversaries using advanced social engineering, generative AI, and rapid identity attacks. The report details surges in vishing, cloud exploitation, and China-nexus activity, and emphasizes the shift toward malware-free, hands-on-keyboard attacks. It provides actionable recommendations for defending against increasingly sophisticated threats across cloud, SaaS, and hybrid environments.
Cybersecurity for the AI era
SOC transformation
To defeat threats, you must transform the SOC by offering next-gen SIEM designed to address the limitations of legacy systems. Harness the power of AI, automation, and blazing-fast search to outpace adversaries.
Adversaries can strike from anywhere, and once in your environment, can move laterally. Bad actors can exploit unmanaged infrastructure and edge devices, while others embed malicious code from within.
Falcon Next-Gen SIEM uses deep adversary expertise to expose and take action on evasive threats.
Cloud detection and response
Modernize cloud security with CDR: unifying cloud posture and protection. Rapid response to security incidents or breaches is imperative for organizations to contain damage and prevent further exploitation. CrowdStrike Cloud Detection and Response (CDR) is a security solution that detects, investigates, and responds to threats like data breaches, insider risks, misconfigurations and more, leveraging advanced intelligence and automation to prevent and mitigate breaches. Slash your response time with automated workflows and drive actionable feedback across teams.
Falcon Cloud Security and AWS
Safeguard your cloud environment with advanced security and real-time threat detection.
Discover how CrowdStrike Falcon Cloud Security accelerates and secures AWS cloud migrations. Learn how CrowdStrike’s integration with the AWS Migration Acceleration Program (MAP) delivers unified security, automated deployment, and proactive threat protection across every migration phase. FCS helps organizations maintain a strong security posture, leverage real-time threat hunting, and protect hybrid, multi-account AWS environments with ease.
Identity protection
CrowdStrike Falcon Identity Protection delivers unified, real-time defense against identity-based attacks across on-premises, cloud, and hybrid environments. Leveraging AI and behavioral analytics, Falcon Identity Protection detects and stops adversaries by correlating identity, endpoint, and data signals, exposing anomalies, and enabling rapid automated response. See how your organization can benefit from comprehensive visibility, risk-based MFA, and just-in-time access, all managed through a single platform and agent.

 Canada (en)
Canada (en)
 Canada (fr)
Canada (fr)
 EU / EFTA
EU / EFTA
 United Kingdom
United Kingdom
 France
France
 India
India