Join Trellix for a tabletop exercise, live demo, and networking at our Ransomware Detection and Response Master Class
Protecting and propelling customers into the future
Trellix and SHI help businesses protect themselves from dynamic and complex security threats with integrated solutions that provide faster response times. Together, we are committed to providing resilient security so your SecOps teams can take proactive steps against potential attacks, allowing your business to focus on its ambitions. Our mission is to enable maximum protection for our customers without sacrificing their ambition.
Trellix CEO, Bryan Palma talks about technology, and the evolution of cybersecurity.
Benefits of Trellix solutions through SHI
Learning and adapting
Our living XDR ecosystem harnesses the power of AI/ML to adaptively strengthen detection, plus responds in real time to active threats, so your business continues as usual.
Native and open
Our flexible, scalable platform with open APIs integrates seamlessly with your existing technologies, to deliver maximum visibility, control, and vendor choice.
Expert and embedded
Our experts monitor and research threats and campaign activities, producing insightful and actionable threat intelligence on threat actors and their behavior.
Endpoint security
Trellix Endpoint Security learns and adjusts proactively through a continuous cycle of prevention, detection, and response against new threats and current attacks.
Keep your organization resilient with adaptive prevention that adjusts and responds in machine time to threats. Customers trust 75M endpoints to Trellix.
Protect and empower your workforce with an integrated security framework that protects every endpoint. Trellix Endpoint Security (ENS) solutions apply proactive threat intelligence and defenses across the entire attack lifecycle to keep your organization safer and more resilient.
The next evolution of endpoint protection
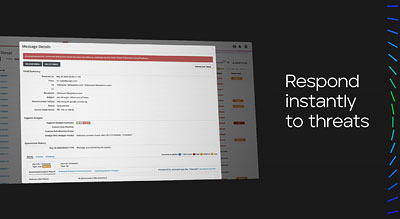
Security operations and analytics
With Trellix Security Operations, you can make your organization more resilient and confident. Filter out the noise and cut complexity to deliver faster, more effective SecOps. Integrate your existing security tools and connect with over 650 Trellix solutions and third-party products.
The need for effective SecOps solutions
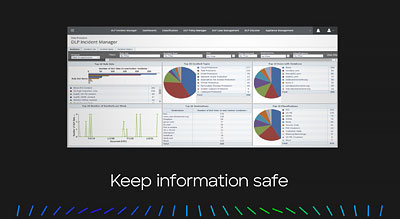
Data protection
Keep your information safe with a single integrated suite. Trellix Data Protection empowers your enterprise to discover, monitor, and protect sensitive data, centralize management and reporting, and synchronize on-premises and cloud policies. Gain confidence that your sensitive data is safe with Trellix Data Protection solutions.
Complete, intelligent data security
Increasing business and regulatory demands are placing pressure on organizations to ensure data security across the enterprise—in data centers and on devices. To keep your information safe and compliant, you need adaptable and complete data security.
Network security
Protect networks, servers, and data centers with a living, learning solution. Trellix Network Security helps you detect the undetectable and stop evasive attacks. Trellix Network Security helps your team focus on real attacks, contain intrusions with speed and intelligence, and eliminate your cybersecurity weak points.
Protect across your network to the cloud
Email Security
Identify and mitigate advanced email threats — including ransomware, business email compromise (BEC), and phishing — with Trellix Email Security. You’ll get leading detection and response capabilities to build a trusted, resilient email environment.

 Your browser is no longer supported
Your browser is no longer supported